Deep Dive: Exploring Hidden Web & Free Tools - Read Now!
Is the digital frontier truly boundless, or are we merely navigating a series of carefully curated illusions? The very architecture of the internet, from its surface layers to the shadowy depths, is undergoing a profound transformation, a shift where the lines between what is visible and what is concealed are blurring at an unprecedented rate.
The digital landscape has become a battleground, where information both authentic and fabricated wages war for our attention. The rise of technologies like deepfakes, sophisticated AI-driven content creation, and the increasing prevalence of deceptive practices necessitates a careful examination of the terrain. We are at a pivotal moment where our understanding of the internet, and indeed, our perception of reality itself, is being fundamentally reshaped.
Let's take a look at the term "deepfakes." Deepfakes, by definition, are synthetic media where a person in an existing image or video is replaced with someone else's likeness. These are being generated using advanced machine learning techniques, they are growing in sophistication and impact, making the ability to distinguish reality from illusion increasingly difficult. The technology itself is neutral, but the applications are anything but. From harmless entertainment to malicious intent, deepfakes are finding their way into every corner of the digital sphere, raising serious questions about trust, authenticity, and the very fabric of truth.
The anonymity afforded by the internet, combined with the speed at which misinformation can spread, creates a perfect storm for manipulation. The creation of realistic-looking content, often targeting vulnerable individuals or groups, is alarming. The potential for damage to reputations, political destabilization, and the erosion of public trust is significant. The lack of robust regulation and the slow pace of technological advancements in identifying and countering deepfakes only exacerbate the problem.
The phrase "a password reset link will be sent to you by email" echoes across the digital landscape. It's a common phrase, a necessary function for security, yet it serves as a stark reminder of our vulnerability. Passwords, while essential, are the first line of defense against digital threats. The ease with which they can be compromised or forgotten highlights the constant need for vigilance and the evolution of more secure authentication methods. Multi-factor authentication, biometric logins, and password managers are becoming the standard as users seek to safeguard their online identities.
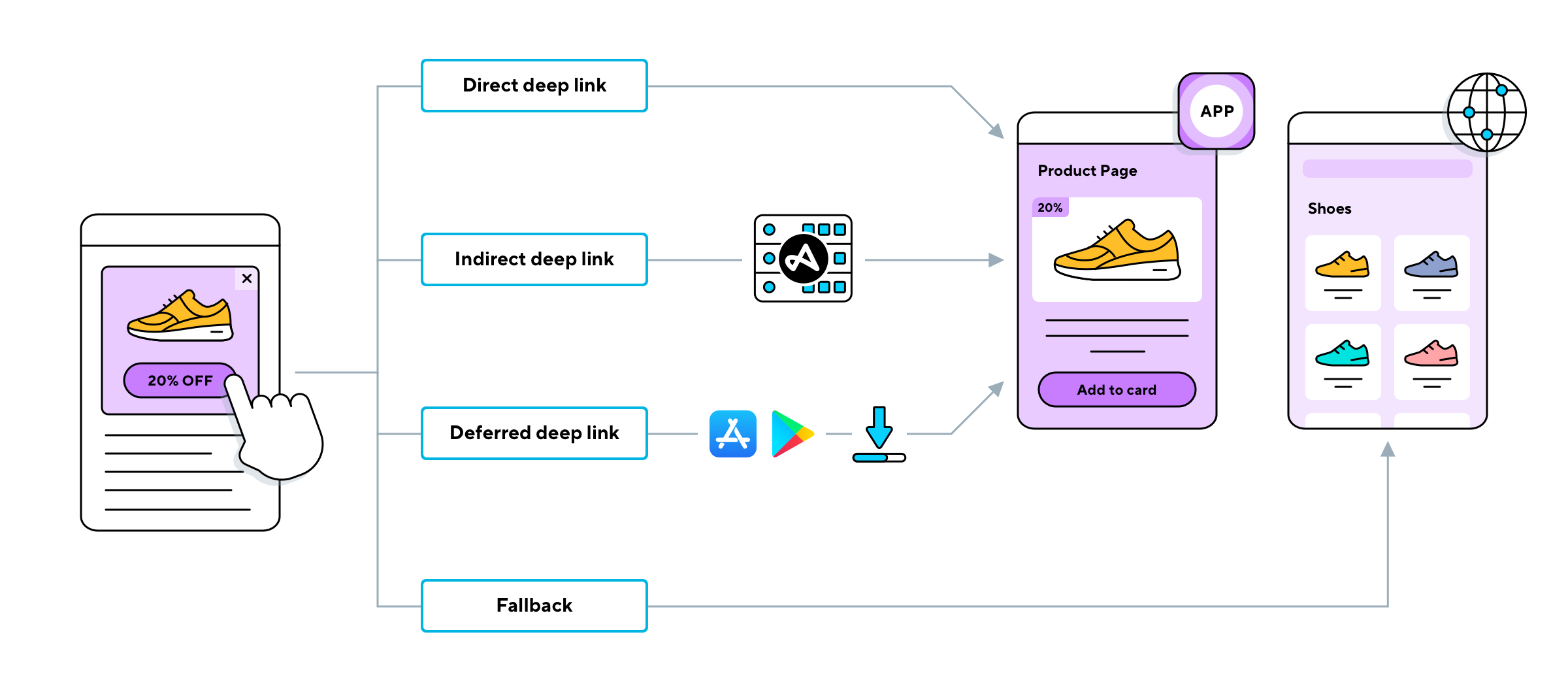
The world of e-commerce provides another interesting case study. The use of deephot links in shopping apps, recommending related products based on a users browsing history, is the perfect example of how algorithms are being used to influence our buying habits. These links, often appearing subtly, guide users towards curated collections of similar products. This method, while effective for businesses seeking to increase sales, also raises questions about transparency and the potential for manipulation. The more we know about how these links work, the better equipped we are to make informed decisions.
The assertion that "deephot.link bridges the gap between the surface web and the deep web, offering users a safe and secure way to explore the internets hidden treasures warrants careful examination. While exploration is part of the internet's allure, it is important to emphasize the risks. The Deep Web, a part of the internet not indexed by standard search engines, contains a wealth of information, but also a great deal of illicit material. This makes it vital to exercise caution and seek guidance from trusted resources before venturing into the unknown.
The notion that deferred deep links can direct the user to specific content, regardless of whether the application is installed or not, is a testament to the constant advancement of technology. Once the application is downloaded, the link will direct users to the intended content. This streamlined process enhances user experience and is an increasingly common practice within the digital ecosystem. They are used by the developers to improve their applications.
Finally, the ability to "connect to any computer at any time" and access files remotely, with claims of smoothness and free personal use, paints a picture of technological convenience. However, it is important to weigh these benefits with considerations for security and privacy. The more we rely on these technologies, the more we must ensure that our data is safe and that our privacy is protected. The world of computer accessibility is evolving rapidly.
In summary, the digital world we inhabit is ever-changing. We must remain vigilant in the face of increasing complexity and potential deception, and seek to understand how the digital landscape operates in order to navigate these challenges and take advantage of the many benefits that this technology offers. The key lies in informed awareness, critical thinking, and a willingness to embrace a new digital literacy to thrive in the modern world.